In today’s digital landscape, the threat of ransomware looms large. This malicious software can wreak havoc on individuals, businesses, and organizations, holding valuable data hostage until a ransom is paid.
To protect yourself and your valuable information, you must be equipped with the knowledge and tools necessary to detect and remove ransomware effectively. Detecting ransomware early on is vital for minimizing damages.
The Case
While reviewing the firewall logs, I stumbled upon something alarming. A network connexion attemps from a local IP address to a Command and Control (CnC) server caught my attention.
These servers are known for delivering encryption keys to ransomware, which encrypts user files and demands a ransom for the decryption key. Fortunately, the enterprise firewall promptly blocked this connection, but it raised concerns about the potential vulnerability of the whole enterprise network.
In this article, we will explore the steps to identify and eliminate ransomware threats, emphasizing the importance of a robust firewall, user education, and reliable antivirus software.
Identifying Suspicious Connections
Upon inspecting the firewall’s security log, it became evident that the local IP address had been attempting to connect to the IP 208.100.26.234 on TCP port 80 every 30 minutes. The firewall’s IPS module flagged this traffic as malicious and effectively dropped the packets.

This incident serves as a reminder that maintaining an up-to-date firewall is crucial for network protection.
Determining the Source Process
To trace the process responsible for sending the packets to the Command and Control (C&C) server, I followed the recommended approach by Mark Russinovich: “When in doubt… run Process Monitor.”
On the computer, which is trying to communicate with the C&C server, I started process monitor and capturede data for a few moments. Then, I performed a search on the IP address 208.100.26.234 (the C&C server IP), which revealed the culprit: rafdpklsxd.exe.
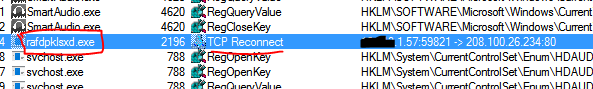
This malicious program likely infected the computer through a disguised email attachment, often in the form of a macro-embedded MS Word document.
It’s important to note that we have witnessed a surge in similar email-based attacks recently.
User Education and Best Practices
If you are responsible for managing your company’s security, it is crucial to educate users about the risks associated with opening attachments in emails from unknown senders. These seemingly harmless files can unleash devastating ransomware attacks.
By emphasizing best practices such as exercising caution when handling email attachments, we can significantly mitigate the threat.
Antivirus Software and System Integrity
One question that arises is why the antivirus software failed to detect and stop this malware.
Unfortunately, in this instance, the antivirus on the affected PC was not functioning properly. Thankfully, the enterprise firewall effectively fulfilled its role in preventing a catastrophic loss of files.
Therefore, it is imperative to ensure that your antivirus software is not only installed but also updated and running optimally.
Closing words
To effectively combat the ransomware threat, organizations must prioritize user education, deploy a robust firewall, and maintain reliable antivirus software.
By raising awareness about the risks associated with email attachments from unknown senders and implementing stringent security measures, we can minimize the chances of falling victim to ransomware attacks.
Remember, constant vigilance and adherence to best practices are essential in safeguarding your network from these pervasive threats.
